Microsoft's Security Vision: Let Our Acronyms Scan All Your Things
Microsoft presented their modern security vision this past week at Gestalt IT’s Security Field Day 7. They highlighted the importance of interconnectedness as a security practice as part of their “SIEM+XDM” security vision. The technology is compelling, but questions about manageability (and cost) remain.
Security Field Day
This article was inspired by a Microsoft presentation I attended as a part of Gestalt IT’s Security Field Day 7 event. More details, including recordings of the sessions, are available at techfieldday.com/event/xfd7/ as well as through searching the event’s twitter hashtag, #XFD7. I also wrote a little more about XFD7 here.
SIEM+XDR, or: Plumbing and Scanning the Interconnectedness of All Things
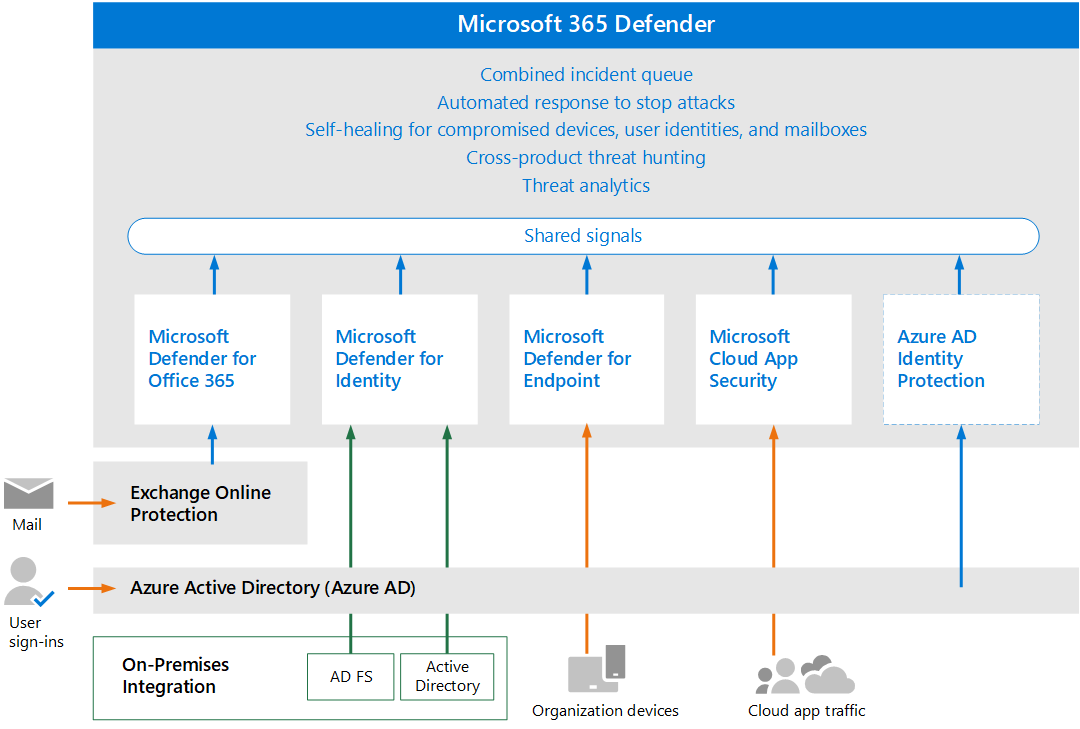
The products Microsoft highlighted at XFD7 have names that are probably familiar to people; the big pitch was how they all should work together. Microsoft’s proposal was this: Intune and AD for policy and IAM, Defender for EDR (endpoint) protection, and Defender for Cloud for your cloud infrastructure protection, with their feisty cloud-based SIEM Sentinel providing visibility and threat protection. Individually, the story goes, all these things will improve an organizations’ security posture, but so much more information can be gleaned when all these products talk together. I anticipate a lot more about this unified approach to security from Microsoft in the future.

|
Side note: This was a common theme at #XFD7. For security to work at maximum effectiveness, everything has to talk to everything else. Or, at the very least, one thing has to collate all of that data for threat assessment. According to many presenters, the interconnectedness and the (anonymous? we hope?) mass sharing of telemetry data and logs of all the things and actions is an essential part of the modern threat detection process. |
|---|
Defining Terms: Antivirus, EDR, XDR and SIEM
I’m going to sidebar here to define some of these terms, just in case anyone is unclear on what they are and why they are being thrown around. Note that these terms are generic; many companies provide EDR, XDR, and SIEM products and services. I am focusing on the Microsoft products here for the sake of specificity and (if you can believe it) in a genuine attempt to keep the word count down.
Antivirus/Anti-malware
Antivirus/anti-malware is a pre-attack security layer. It scans files based on known signatures and stops them from executing. The old name was simply ‘antivirus’ software. It is becoming more common to use both terms, or even just use anti-malware exclusively.
An example of this is Microsoft Defender Antivirus, which (since at least Windows 10) is built into Windows.
EDR: Endpoint Detection and Response
Advanced protection, specifically focused on the endpoint. This is the modern baseline of device protection and typically relies on installed agents that protect devices on an individual basis. EDR has logging and auditing features that enable security administrators to understand what is happening on an endpoint now, and in the past.
Microsoft Defender for Endpoints is an EDR. It is specifically built for protecting endpoints.
XDR: eXtended detection and response
An all-encompassing security solution that covers resources of all types, across your environment. This includes infrastructure, endpoint, email, applications, and identities. It leverages artificial intelligence (AI) and automation to analyze data and workflows to automatically stop attacks, and quarantine and/or remediate affected assets.
Microsoft Defender is an XDR. Defender for Endpoint is one of many products that fall under the Defender umbrella.
SIEM: Security Information and Event Management
A SIEM is a single centralized system that allows full visibility into your entire environment. It collects data from as wide a range of sources as possible and analyzes it to provide real-time insights and alerts that would be impossible to do manually.
Microsoft Sentinel is a (cloud-based) SIEM.
The scope of the data Microsoft (and their customers) have to work with is legitimately huge
When it comes to security, Microsoft’s killer feature (according to them, of course) is their massive, massive install base, and their product interconnectivity. Because of this scale, Microsoft has been known to refer to themselves as ‘the largest security shop in the world.’
This first point is of course unquestionably true. Microsoft essentially owns the desktop market, with the 2nd largest Cloud footprint around, and Office 365 dominates the markets of office productivity and business intelligence. By default, these products all report home to Microsoft about all users, and by extension, all threats.
And some of the numbers are pretty staggering: Just in 2020, they analyzed 300B identity logins, 4.1B O365 user actions, and 3.2B Admin actions. They stated, and this is an exact quote “Microsoft is second to none when it comes to attack diversity,” which is probably true for a lot more reasons than just their Windows hegemony.
There are a lot of organizations that use Microsoft products… 650,000 or so, according to Microsoft themselves. All in all, they talk about an aggregate of 24 trillion threat signals every day going through these organizations’ deployments. If we divide these evenly, we get 37,500,000 threat signals per organization, per day. So of course AI/ML comes into play here, because as they highlighted, these are numbers that are impossible for humans to deal with.
What does a fully deployed Microsoft Threat detection Model look like?
According to Microsoft, an organization should have: an outside-in protection scheme, an inside-out protection scheme, and Sentinel to tie it all together.
- Outside-in: firewalls, application load balancers, and intrusion detection systems form the crusty outer shell. Antivirus and EDR protects individual devices. This protects your organization from as many of those threat actions as possible.
- Inside-out: users try to do things everywhere, they’re only allowed to do the bare minimum, following a Zero Trust model. This protects attackers who have gotten in from moving laterally, and ideally also protects data from exfiltration by bad actors, be they malware-based, or insider threats.
- Oversight: everything is logged into Sentinel, analyzed in real time, and with all these tools working together, bad actors are shut down immediately.
Maximizing Sentinel’s effectiveness means tying in logs from as many places as possible, and Microsoft is doing their utmost to make sure that can happen. Sentinel has the ability to ingest logs from a lot of other providers using an ever-expanding list of connectors. When all else fails, you can configure a Linux system to do syslog forwarding until a direct connector exists. This is important- a lot of legacy systems/devices/shops are already setup this way, so it would be trivial to redirect or mirror outgoing logs to Sentinel.
(Also, please note that “Microsoft Defender for Cloud” is not the same thing as Microsoft Defender for Cloud Apps.”)
More on Microsoft Defender for Cloud
Previously known as Azure Security Center and Azure Defender, Defender for Cloud is a tool intended to support infrastructure security in and of the cloud. It is heavily focused on Azure, although it does have some ability to support infrastructure in AWS and GCP (specifically IaaS and Kubernetes instances. Microsoft Defender for Cloud does vulnerability assessments and scans.
A part of Defender for Cloud is Microsoft Defender for servers, which includes Microsoft Defender for Endpoint for your IaaS server-level protection needs. (This is one way that Defender for Cloud extends to AWS and GCP- you install this on your Windows or Linux instances.)
Defender for Cloud is also aware of your cloud configurations. Existing Azure Policies are checked and changes recommended based on the Azure Security Benchmark, allowing Microsoft Defender for Cloud to apply security standards across your protected resources. And of course, everything communicates back to Sentinel.
Microsoft also just released a Ransomware Recommendations dashboard that leverages Defender for Cloud plus Secure Score, Azure Security, and a few other tools, to provide specific recommendations around Ransomware. I have not had time to look at it yet, but I feel that this does show some initiative on Microsoft’s part to flesh out the offerings that utilize Defender for Cloud.
Advanced Threat Analysis in the Defender Portal
There are two ways of running analyses of alerts/incidents in a Defender-based system. You can query the threat analytics in Microsoft 365 Defender system through both a comprehensive threat analytics dashboard, or more advanced hunting using the “Kusto Query Language,” or KQL. This is pretty interesting, especially for threat hunting or postmortems, and deserves its own separate post. I include it here with the link to the Microsoft product page just to make clear that this capability exists.
(One last point: since I am losing the war against people who simply live for pronouncing the obviously unpronounceable and insist on calling SQL “Sequel,” I will now forever be pronouncing KQL as “Keyquel.” I hope you will join me on my epic quest.)
Final Thoughts: What about management and cost?
One thing that didn’t really get covered was ‘how do we manage this stuff?’ And just as importantly, ‘how do we pay for it?’ These tools are from all over the Microsoft map, with different teams, different pricing models, etc. Some of them are purchases, some are built-in. Microsoft made great hay about how you could use just Microsoft, instead of 50+ other tools. But the problem is, Microsoft’s internal teams do not historically talk to each other, or even seem to recognize each other’s existence. How many Admin portals are we talking about here? Wouldn't this just be swapping 50+ external tools for a different 50 tools that are all collected under the Microsoft banner?
On top of this, Microsoft’s licensing requirements are hard enough to decipher at the best of times. Now you’re adding in dynamic cloud costs like data flows, data storage, analysis, queries, etc., that make it very hard to determine what a bill is going to look like. How are we expected to audit this usage, and make sure that we are 1) properly licensed, and 2) not wasting money on licenses we don’t need? The answer can’t just be “E5’s for everybody!” A cynical person would say that the confusion is part of the financial model, you know: “make it so confusing that people just buy the most expensive tier.”
The strength of the technology itself is not the end of the discussion. An important axiom in security management is that the cost of the protection cannot exceed the value of the items being protected. And management costs- time invested in choosing, testing, deploying, and managing- have to be taken into consideration too. Big shops that are already invested in Microsoft will see all of this as a logical next step. Because of the questions above, I can still see quite a few shops (of all different sizes) being hesitant.